What is AWS Cloud Formation?
AWS Cloud Formation is an AWS service that helps to automate the setup of AWS resources using template files.
We create a template that describes all the AWS resources that we need (like Amazon EC2 instances or Amazon RDS DB instances), and CloudFormation takes care of provisioning and configuring those resources for us.
If you have worked with Docker, then you create one docker-compose.yaml file where we defines all the services that we need to run right, Cloud Formation is just like the same concept for the AWS resources.
AWS CloudFormation enables you to manage your complete infrastructure or AWS resources in a text file, or template. A collection of AWS resources is called a stack. AWS resources can be created or updated by using a stack.
All the resources you require in an application can be deployed easily using templates. Also, you can reuse your templates to replicate your infrastructure in multiple environments. To make templates reusable, use the parameters, mappings and conditions sections in the template so that you can customize your stacks when you create them.
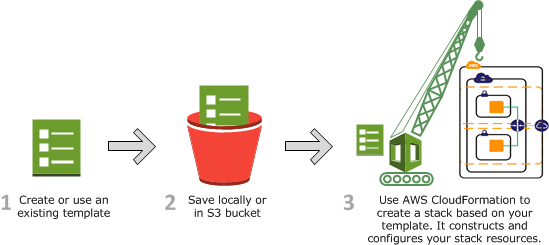
- Create a new template or use an existing CloudFormation template using the JSON or YAML format.
- Save your code template locally or in an S3 bucket.
- Use AWS CloudFormation to build a stack on your template.
- AWS CloudFormation constructs and configures the stack resources that you have specified in your template.
How does AWS CloudFormation work?
-
When creating a stack, AWS CloudFormation makes underlying service calls to AWS to provision and configure your resources.
-
CloudFormation can only perform actions that you have permission to do. For example, to create EC2 instances by using CloudFormation, you need permissions to create instances.
-
You’ll need similar permissions to terminate instances when you delete stacks with instances. You use AWS Identity and Access Management (IAM) to manage permissions.
Source: AWS Doc
Use the AWS CloudFormation Designer or your own text editor to create or modify a CloudFormation template in JSON or YAML format.
Save the template locally or in an Amazon S3 bucket. If you created a template, save it with a file extension like: .json, .yaml, or .txt.
Create a CloudFormation stack by specifying the location of your template file, such as a path on your local computer or an Amazon S3 URL. If the template contains parameters, you can specify input values when you create the stack. Parameters allow you to pass in values to your template so that you can customize your resources each time you create a stack.
You can create stacks by using the CloudFormation console, API, or AWS CLI.
{
"AWSTemplateFormatVersion": "2010-09-09",
"Description": "A simple EC2 instance",
"Resources": {
"MyEC2Instance": {
"Type": "AWS::EC2::Instance",
"Properties": {
"ImageId": "ami-0ff8a91507f77f867",
"InstanceType": "t2.micro"
}
}
}
}
AWSTemplateFormatVersion: 2010-09-09
Description: A simple EC2 instance
Resources:
MyEC2Instance:
Type: 'AWS::EC2::Instance'
Properties:
ImageId: ami-0ff8a91507f77f867
InstanceType: t2.micro
Updating a stack with change sets
-
When you need to update your stack’s resources, you can modify the stack’s template. You don’t need to create a new stack and delete the old one.
-
To update a stack, create a change set by submitting a modified version of the original stack template, different input parameter values, or both.
-
CloudFormation compares the modified template with the original template and generates a change set. The change set lists the proposed changes. After reviewing the changes, you can start the change set to update your stack or you can create a new change set.

-
You can modify a CloudFormation stack template by using AWS CloudFormation Designer or a text editor. For more information, see Modifying a stack template .
-
Save the CloudFormation template locally or in an S3 bucket.
-
Create a change set by specifying the stack that you want to update and the location of the modified template, such as a path on your local computer or an Amazon S3 URL. If the template contains parameters, you can specify values when you create the change set. For more information about creating change sets, see Updating stacks using change sets .
-
View the change set to check that CloudFormation will perform the changes that you expect.
-
Initiate the change set that you want to apply to your stack. CloudFormation updates your stack by updating only the resources that you modified and signals that your stack has been successfully updated. If the stack updates fails, CloudFormation rolls back changes to restore the stack to the last known working state.
Deleting a stack
-
When you delete a stack, you specify the stack to delete, and CloudFormation deletes the stack and all the resources in that stack.
-
You can delete stacks by using the CloudFormation console, API, or AWS CLI.
-
If you want to delete a stack but want to retain some resources in that stack, you can use a deletion policy to retain those resources.
{
"AWSTemplateFormatVersion" : "2010-09-09",
"Resources" : {
"myS3Bucket" : {
"Type" : "AWS::S3::Bucket",
"DeletionPolicy" : "Retain" <-- Here retain
}
}
}
AWSTemplateFormatVersion: '2010-09-09'
Resources:
myS3Bucket:
Type: AWS::S3::Bucket
DeletionPolicy: Retain <-- Here retain
AWS CloudFormation Concepts
An AWS CloudFormation template is a formatted text file in JSON or YAML language that describes your AWS infrastructure. To create, view and modify templates, you can use AWS CloudFormation Designer or any text editor tool.
An AWS CloudFormation template consists of nine main objects:
- Format version: Format version defines the capability of a template.
- Description: Any comments about your template can be specified in the description.
- Metadata: Metadata can be used in the template to provide further information using JSON or YAML objects.
- Parameters: Templates can be customized using parameters. Each time you create or update your stack, parameters help you give your template custom values at runtime.
- Mappings: Mapping enables you to map keys to a corresponding named value that you specify in a conditional parameter. Also, you can retrieve values in a map by using the “Fn::FindInMap“ intrinsic function.
- Conditions: In a template, conditions define whether certain resources are created or when resource properties are assigned to a value during stack creation or updating. Conditions can be used when you want to reuse the templates by creating resources in different contexts. You can use intrinsic functions to define conditions. In a template, during stack creation, all the conditions in your template are evaluated. Any resources that are associated with a true condition are created, and the invalid conditions are ignored automatically.
- Transform: Transform builds a simple declarative language for AWS CloudFormation and enables reuse of template components. Here, you can declare a single transform or multiple transforms within a template.
- Resources: Using this section, you can declare the AWS resource that you want to create and specify in the stack, such as an Amazon S3 bucket or AWS Lambda.
- Output: In a template, the output section describes the output values that you can import into other stacks or the values that are returned when you view your own stack properties. For example, for an S3 bucket name, you can declare an output and use the “Description-stacks” command from the AWS CloudFormation service to make the bucket name easier to find.
Learn more about the template anatomy
AWS Intrinsic Functions
AWS CloudFormation provides several built-in functions that help you manage your stacks. Use intrinsic functions in your templates to assign values to properties that are not available until runtime.
- Fn::Base64
- Fn::Cidr
- Condition functions
- Fn::FindInMap
- Fn::GetAtt
- Fn::GetAZs
- Fn::ImportValue
- Fn::Join
- Fn::Length
- Fn::Select
- Fn::Split
- Fn::Sub
- Fn::ToJsonString
- Fn::Transform
- Ref
AWS Conditions Functions
-
You can use intrinsic functions, such as
Fn::If,Fn::Equals, andFn::Not, to conditionally create stack resources. These conditions are evaluated based on input parameters that you declare when you create or update a stack. -
After you define all your conditions, you can associate them with resources or resource properties in the Resources and Outputs sections of a template.
-
- You can use the following functions in the Fn::If condition:
- Fn::Base64
- Fn::FindInMap
- Fn::GetAtt
- Fn::GetAZs
- Fn::If
- Fn::Join
- Fn::Select
- Fn::Sub
- Ref
- Fn::Not
- Fn::Or
You can use the following functions in all other condition functions, such as Fn::Equals and Fn::Or :
Benefits of AWS CloudFormation
-
Deployment speed: When you create CloudFormation templates to manage how AWS resources are configured and deployed, you can deploy multiple instances of the same resources almost instantaneously using just one template. This approach leads to much faster deployment than you could achieve if you had to manually set up each deployment by running commands on the CLI or pressing buttons in the AWS console.
-
Scaling up: Even if you do not initially expect to deploy multiple instances of the same AWS resources, CloudFormation templates are useful because they ensure that you can scale your environment up quickly when the time comes. By keeping CloudFormation templates on hand, you will know that you can add more virtual machine instances or storage space, for example, at a moment’s notice if your applications experience increased traffic and you need to scale your environment up.
-
Service integration: A single CloudFormation template can manage the deployment of individual services or resources and multiple resources. This management ability means you can use CloudFormation to integrate different AWS cloud services. For example, you could write a template that sets up an EC2 virtual machine within an AWS Virtual Private Cloud (VPC) or deploys an S3 storage bucket and configures access control for it using the IAM service.
-
Consistency: When you use CloudFormation templates to define and deploy AWS resources, you can apply precisely the same configuration repeatedly. In this way, CloudFormation ensures that your applications and services will be consistent and identical, no matter how many instances you create.
-
Security: Along similar lines, although CloudFormation is not a security tool per se, it can improve the overall security of your AWS environment by reducing the risk of oversights or human errors that could turn into breaches. As long as you design your CloudFormation templates to be secure, you do not need to worry that an engineer who deploys resources will forget to turn on important access control, for example, or leave data exposed to unrestricted, public access.
-
Easy updates: In addition to deploying new resources, you can apply changes to existing resources with CloudFormation templates. This ability simplifies the process of, for example, adding more storage to a fleet of ec2 instances or changing access control rules.
-
Auditing and change management: When you use CloudFormation to manage your infrastructure, you can track changes based on which templates you have applied and how they change over time. Change tracking in CloudFormation means that you will be able to determine how your AWS services and resources have changed over time without looking through logs to reconstruct the timeline of updates.